A new report of Lumen Technologies discovers hackers are targeting Wi-Fi routers to get access to all of your connected gadgets. The report came from Black Lotus Lab which is a security department of Lumen Technologies. It all began at the start of the pandemic in the year 2020 when millions of people started working from home. The details of the report served many attacks on small home/home office (SOHO) routers. It doesn’t benefit that this malware is just two years old because it’s been gradually corrupting routers since 2020. ZuoRAT is a part of a broader hacking campaign that has occurred since the fourth quarter of 2020 and continues to regulate. This malware is exceptionally sophisticated.
Till now, investigators from Lumen Technologies of Black Lotus Labs explain that they’ve specified at least 80 targets infected by this complicated malware. ZuoRAT gets remote access to the small business routers. It is continually scanning webs for weak and vulnerable routers and strikes if one is found.
ZuoRAT can pivot damage to all connected devices using one of the two techniques. Below are the two possible methods:
- DNS hijacking: In this technique, valid IP addresses can be replaced by communicating to a domain such as Google or Facebook with a malicious one regulated by the attacker.
- HTTP hijacking: In this technique, the malware injects itself into the connection to develop a 302 error that pivots the user to another IP address.
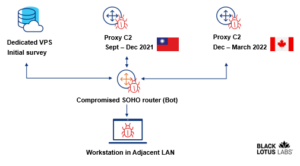
This visual demonstrates the steps listed involved in the attack:
Black Lotus Labs Research on This Sophisticated Malware
According to a report by Black Lotus Labs, the attackers operate Remote Access Trojans (RATs) to seize a home’s router. The trojans use a unique malware called ZuoRAT to get access and then enter inside the router. After deployment, the RATs enable hijackers to upload and download files to all the connected devices on the same network. ZuoRAT often gets installed by influencing unpatched susceptibility in SOHO devices. It compiles DNS lookups and network traffic which are some extremely sensitive data.
Researchers of Lumen Technologies believe that it may arise from a nation-state performer which means that an administration with a lot of resources could be targeting SOHO routers in North America and Europe. This refined hacking group has been infecting a wide range of routers in Europe and North America. It operates with malware that holds entire control of all the connected devices like Windows, macOS, and Linux.